 With the summer season in full swing, you probably have some free time on your hands. If you’re like most people, you’ve probably taken a trip or two (or a staycation) and read some books that had been on your to-do list for awhile. But, the most important thing you should do this summer is follow my top ten summer security tips.
With the summer season in full swing, you probably have some free time on your hands. If you’re like most people, you’ve probably taken a trip or two (or a staycation) and read some books that had been on your to-do list for awhile. But, the most important thing you should do this summer is follow my top ten summer security tips.
TIP 1
If you travel, whether to a nearby hotel, or halfway around the world, save your photos to share when you return home. Don’t post any photos that indicate you’re away from home. Even if you think only friends and family may see the pics, THEY can share them. Don’t give thieves the opportunity to visit your house uninvited. Automatically upload your photos to iCloud or Google’s photo app after you take them. This way, if you lose your phone, you will still have access to all the photos you’ve taken.
TIP 2
The other half of the first tip is to review and update your privacy settings on your social sites – before you travel, or before you start sharing lots of posts. There is “metadata” imbedded in your photos that will indicate your location, time, and even what device you are using. Follow your device’s instructions on how to eliminate that information.
TIP 3
Create a free email address to use when traveling. That way, you can delete it or forget about it once you return home. Since you don’t know how a faraway hotel, restaurant, or museum will secure its data, play it safe. This way, you can sign up for discounts or giveaways without endangering your real email addresses. This is easily set up using Gmail.
TIP 4
Since it’s best to be safe than sorry, change your passwords regularly – every couple of months. This means, email accounts, social media accounts, financial websites, etc. And don’t use the same password twice. Use a password manager like LastPass to store your passwords and create new ones. This way, you only have to remember only one password.
TIP 5
Clean up the apps on your smartphone and tablet. Do you still play Angry Birds? How many weather apps do you really need? Your may be surprised if, after deleting some apps, your device runs faster. Be sure that you only download apps from your legitimate app store. Using third party app stores can lead to downloading malware, since third party app stores do not necessarily police the apps they host.
TIP 6
With summer sales (including Amazon’s recent Prime Day), you will be tempted to shop online. Rule number one: Don’t ever click on the “Remember Password” option in your browser. Unlike passwords saved in LastPass, or other password managers, they are not protected by encryption and are open for bad guys to see if they get ahold of your browser. To quote Dana Molina of SureTech, “If your device is ever stolen, you’ve just invited a thief into your home, removed their shoes, and given them a foot massage.”
TIP 7
Treat your personal data as if it were cash, and never share it with just anyone. Your Social Security number, credit card numbers, and bank account numbers can be used to steal your money or open new accounts in your name. Therefore, every time you are asked for your personal information, whether in an email, text, phone message, or web form or survey, think about whether you can really trust the request. In an effort to steal your information, scammers will do everything they can to appear trustworthy. This may seem like a strange thing to say, but “when in doubt, LIE” about the information you are providing in a web form or to establish a social media account. For example, don’t use your real birthdate. Instead, use January 1 plus five years younger or older than you really are. Of course, there are official sites that may require your real data, but for everything else, be creative.
TIP 8
Using a public Wi-Fi network not only puts your personal devices at risk, but also exposes your traffic to everyone else using the same network. Cybercriminals can potentially access any information you provide, such as, credit card numbers, confidential information, or passwords. If you are at a place with free Wi-Fi, be sure you use a virtual private network (VPN) to protect yourself online. There are free VPN’s on the market, such as, the updated TOR app, that will enable you to browse safely.
TIP 9
The physical security of your devices is just as important as their technical security. If you need to leave your laptop, phone, or tablet for any length of time, lock them up so no one else can use them. Also use biometrics if your device has the capability, or use a screen saver password, and be sure to turn on the “Find My Device” feature that most wireless devices have. And most important of all, encrypt your device so that if someone does steal it, he or she cannot gain access to your data.
TIP 10 (actually Tip 10 plus an extra tip)
Lastly, I cannot make a security tip list without including the two most important tips in the data breach prevention toolbox: Before any account is hacked and before you lose your data, back up, back up, back up. And as a result of the world we live in, a new mantra has been added; It’s not if you get hacked, it’s when, so be sure to install anti-virus software on all of your wireless devices.
Before Facebook (yes, we really had a life before Zuck’s online platform), we didn’t share everything online. We didn’t announce our trips while we were away from home. We didn’t post photos of babies before they left the hospital. And we didn’t post every single status update. So, bottom line, think before posting, and maybe, it would be helpful to consider consequences if a security breach happens and a hacker accessed your email account or your favorite social media account. Would you be in crisis mode, or just shake it off because none of your sensitive data was posted? Hopefully, after reading this post and reviewing your content, you can answer the latter.
What’s your favorite summer security tip?
Image Credit: Sai Kiran Anagani via Unsplash.



 With the summer season in full swing, you probably have some free time on your hands. If you’re like most people, you’ve probably taken a trip or two (or a staycation) and read some books that had been on your to-do list for awhile. But, the most important thing you should do this summer is follow my top ten summer security tips.
With the summer season in full swing, you probably have some free time on your hands. If you’re like most people, you’ve probably taken a trip or two (or a staycation) and read some books that had been on your to-do list for awhile. But, the most important thing you should do this summer is follow my top ten summer security tips. How often do you read email notifications from your frequently used social media sites? When Facebook makes a change to its news feed, how soon are you aware of the change, and better yet, do you care? When Twitter updates its Terms and Conditions, do you read the new terms and conditions page in its entirety? When a social platform changes or updates its privacy policy, do you read the new policy? You know what I would recommend.
How often do you read email notifications from your frequently used social media sites? When Facebook makes a change to its news feed, how soon are you aware of the change, and better yet, do you care? When Twitter updates its Terms and Conditions, do you read the new terms and conditions page in its entirety? When a social platform changes or updates its privacy policy, do you read the new policy? You know what I would recommend. If you spend your time living and breathing information security, there are some quotes that you share with others on a regular basis. Here are some quotes that provide insight, reminders, and tips.
If you spend your time living and breathing information security, there are some quotes that you share with others on a regular basis. Here are some quotes that provide insight, reminders, and tips. I recently received an unusual email message to my main email account inbox, and my immediate reaction was, “This would be a good topic for a blog post.” As a member of the infosecurity industry, I practice what I preach and do not open emails from senders I don’t recognize. While I, too, may be curious when an email arrives with a tempting subject, I avoid phishing and spam at all costs. This particular email message, though, was different, and here’s why.
I recently received an unusual email message to my main email account inbox, and my immediate reaction was, “This would be a good topic for a blog post.” As a member of the infosecurity industry, I practice what I preach and do not open emails from senders I don’t recognize. While I, too, may be curious when an email arrives with a tempting subject, I avoid phishing and spam at all costs. This particular email message, though, was different, and here’s why.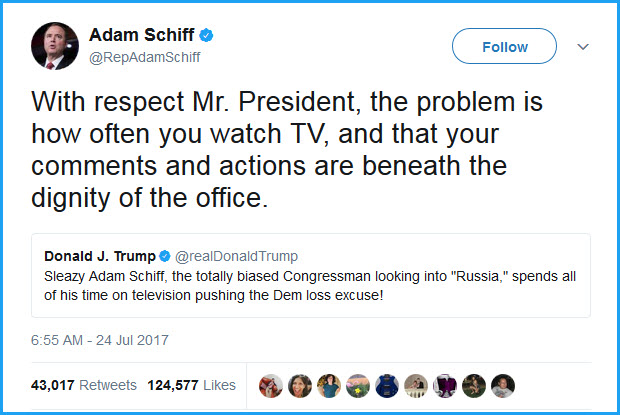
 As a technology blogger and gearhead, I was fortunate to get up close and personal to the newest cars and technologies during one of the media days before this year’s Greater Los Angeles Auto Show. What I found, however, was rather scary.
As a technology blogger and gearhead, I was fortunate to get up close and personal to the newest cars and technologies during one of the media days before this year’s Greater Los Angeles Auto Show. What I found, however, was rather scary. Recently, I saw “I.T.” the movie starring Pierce Brosnan as a visionary CEO named Mike Regan. In the movie, Regan is planning to take his company public, and soon after the movie begins, Regan makes a presentation to a large group at his office, but the presentation goes sideways electronically. An IT expert is called in to help, but too often these days, the IT expert is a temporary employee. This IT temp saves the day and gets all the technology working again, so the presentation is able to move forward. Regan is grateful and becomes friendly with the IT temp. The problem, though, is that this techie is a psycho, and when he’s unable to date Regan’s daughter, he becomes determined to destroy Regan’s life.
Recently, I saw “I.T.” the movie starring Pierce Brosnan as a visionary CEO named Mike Regan. In the movie, Regan is planning to take his company public, and soon after the movie begins, Regan makes a presentation to a large group at his office, but the presentation goes sideways electronically. An IT expert is called in to help, but too often these days, the IT expert is a temporary employee. This IT temp saves the day and gets all the technology working again, so the presentation is able to move forward. Regan is grateful and becomes friendly with the IT temp. The problem, though, is that this techie is a psycho, and when he’s unable to date Regan’s daughter, he becomes determined to destroy Regan’s life. While the eyes of everyone in the technology sector watched the Apple-FBI feud about a key to unlock a terrorist’s iPhone, you should have been watching too. You might wonder why this situation affected you, and the reason is simple. If the government can unlock an allegedly locked phone’s operating system for one phone, it has the potential to unlock anyone’s phone. It’s a slippery slope as to reasons, but there are other things you should consider in this discussion.
While the eyes of everyone in the technology sector watched the Apple-FBI feud about a key to unlock a terrorist’s iPhone, you should have been watching too. You might wonder why this situation affected you, and the reason is simple. If the government can unlock an allegedly locked phone’s operating system for one phone, it has the potential to unlock anyone’s phone. It’s a slippery slope as to reasons, but there are other things you should consider in this discussion.